VTT Technical Research Centre of Finland RoutineMaker Towards End-User Automation
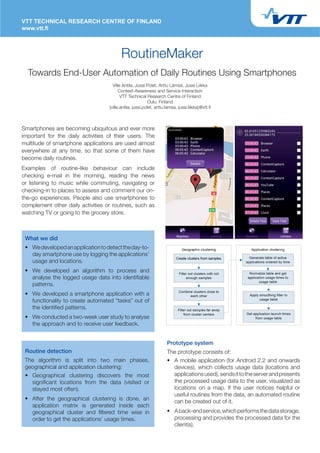
- 1. VTT TECHNICAL RESEARCH CENTRE OF FINLAND www.vtt.fi RoutineMaker Towards End-User Automation of Daily Routines Using Smartphones Ville Antila, Jussi Polet, Arttu Lämsä, Jussi Liikka Context-Awareness and Service Interaction VTT Technical Research Centre of Finland Oulu, Finland {ville.antila, jussi.polet, arttu.lamsa, jussi.liikka}@vtt.fi Smartphones are becoming ubiquitous and ever more important for the daily activities of their users. The multitude of smartphone applications are used almost everywhere at any time, so that some of them have become daily routines. Examples of routine-like behaviour can include checking e-mail in the morning, reading the news or listening to music while commuting, navigating or checking-in to places to assess and comment our on- the-go experiences. People also use smartphones to complement other daily activities or routines, such as watching TV or going to the grocery store. What we did • We developed an application to detect the day-to- day smartphone use by logging the applications’ usage and locations. • We developed an algorithm to process and analyse the logged usage data into identifiable patterns. • We developed a smartphone application with a functionality to create automated “tasks” out of the identified patterns. • We conducted a two-week user study to analyse the approach and to receive user feedback. Prototype system Routine detection The prototype consists of: The algorithm is split into two main phases, • A mobile application (for Android 2.2 and onwards geographical and application clustering: devices), which collects usage data (locations and • Geographical clustering discovers the most applications used), sends it to the server and presents significant locations from the data (visited or the processed usage data to the user, visualized as stayed most often). locations on a map. If the user notices helpful or useful routines from the data, an automated routine • After the geographical clustering is done, an can be created out of it. application matrix is generated inside each geographical cluster and filtered time wise in • A back-end service, which performs the data storage, order to get the applications’ usage times. processing and provides the processed data for the client(s).
