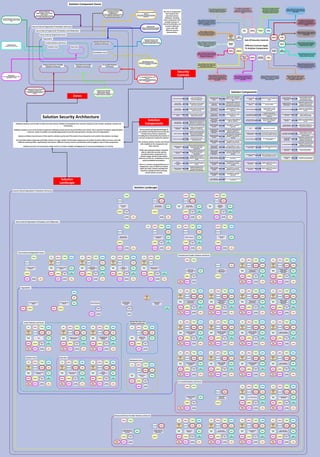
Solution Security Architecture
- 1. Solution Security Architecture Zones Security Controls Solution Landscape Individual solutions must be able to inherit security controls, facilities and standards from common enterprise-level controls, standards, toolsets and frameworks. Individual solutions must not be forced to implement individual infrastructural security facilities and controls. This is wasteful of solution implementation resources, results in multiple non-standard approaches to security and represents a security risk to the organisation. Solution architects must be aware of the need for solution security and of the need to have enterprise-level controls that solutions can adopt. The extended solution landscape potentially consists of a large number of interacting components and entities located in different zones, each with different security profiles, requirements and concerns. Different security concerns and therefore controls apply to each of these components. Solution security is not covered by a single control. It involves multiple overlapping sets of controls providing layers of security. Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Design, implement and operate infrastructure, facilities and processes to ensure the availability of the solution, resilience against component failure and recovery in the event of failure Design, implement and operate tools and processes to manage the security aspects of developed, acquired or externally hosted solutions to identify, prevent, detect and resolve security weaknesses and vulnerabilities Design, implement and operate tools and processes to monitor, analyse and report on the usage of a solution and its constituent components including resource consumption and performance Design, implement and operate tools and processes to collect, store, analyse, alert, review audit logs of solution activity events that to facilitate the detection, understanding and recovery from an attack Design, implement and operate tools and processes for the creation, assignment, management and revocation of access credentials and privileges for solution and data access to administrator, user and service accounts Design, implement and operate tools and processes to monitor, analyse, detect and act-on email-based attacks and email vulnerabilities Design, implement and operate tools and processes to prevent the installation, spread, and execution of malicious applications, code or scripts Design, implement and operate tools and processes to manage solution data and establish data backup and recovery including integrity of backup data Design, implement and operate tools and processes to manage and control the infrastructure and software assets that comprise the totality of solutions in order to actively manage those assets Design, implement and operate tools and processes to assign and manage authorisation to and assignment of credentials for service, administrator and user accounts, including administrator accounts Design, implement and operate tools and processes to ensure the security of infrastructure and software assets through active asset inventory management Design, implement and operate tools and processes to monitor network infrastructure, ensuring only authorised software can be installed and run, and provide defense against security threats and attacks Design, implement and operate tools and processes to test solutions and their infrastructure to identify and resolve vulnerabilities and weaknesses in their design, implementation and operation through the simulation of attacks Design, implement and operate tools and processes to monitor, analyse, detect and act-on browser-based attacks and browser vulnerabilities Design, implement and operate tools and processes to initially assess and continually monitor the security arrangements of solution component suppliers and service providers and the components and services they provide Design, implement and operate tools and processes to design, implement, operate and manage the security of network infrastructure and facilities including their vulnerability Design, implement and operate tools and processes to continuously assess and track vulnerabilities on all solution components in order to identify, response to, remediate and minimise attacks Design, implement and operate tools and processes to identify, classify, securely handle, manage access to, manage regulatory compliance, appropriately retain and dispose of solution data Sets Of Security Controls Different Controls Apply To Solution Components Solution Zone Data Zone Workstation Zone Central Solutions and Access Organisation Remote Business Unit Solutions and Access Co-Located Solutions and Access Outsourced Service Provider Solutions and Access Cloud Service Provider Solutions and Access Secure External Organisation Access Insecure External Organisation Presentation And Access Insecure External Organisation Presentation And Access Where publicly accessible or accessing entities reside. These entities are regarded as insecure and/or untrusted. Secure External Organisation Participation and Collaboration Outside the physical organisation boundary where entities that are provided by or to trusted external parties reside Secure External Organisation Participation and Collaboration Secure External Organisation Access Contain entities that enable secure access or are securely accessible from outside the organisation Organisation Contain the entities within the organisation boundary and contains all the locations, business units and functions within it Remote Business Unit Solutions and Access Remotely located organisation business unit or location and the entities it contains Workstation Zone Zone within the organisation where users accessing data and solutions are segregated for security Co-Located Solutions and Access Contains solutions the organisation has located in facilities provided by co-location providers Central Solutions and Access Contains the solution entities and their data Solution Zone Contains the solution entities Data Zone Zone within the organisation where data is segregated for security Outsourced Service Provider Solutions and Access Contains solutions provided by and located in facilities provided by outsourced partners Cloud Service Provider Solutions and Access Contains solutions - platform, infrastructure and service - provided by and located in cloud service providers Solution Components External Data Telemetry Devices External Public Interacting Parties External Data Sources External Telecommand Devices Private Access Groups External Private Interacting Parties Externally Located Employees Mobile Employees Data Access, Exchange and Service Gateway Secure Communications Access Externally Accessible Solutions Publicly Accessible Solutions Business Continuity and Disaster Recovery Network Monitoring Access and Activity Logging Externally Accessible Infrastructure Deployed Solutions Identity, Access and Authentication Internally Accessible Infrastructure Deployed Solutions Internally Accessible Infrastructure Deployed Solutions Data Stores Publicly Accessible Infrastructure Deployed Solutions Anti-Virus, Malware Defense Threat Protection and Vulnerability Checking Cloud Service Provider Connectivity and Access Cloud Service Provider Access and Authentication Externally Accessible Infrastructure Deployed Solutions Data Stores Publicly Accessible Infrastructure Deployed Solutions Data Stores Backup and Recovery Identity, Access and Authentication Mail Solution Unstructured Data Stores Solution Structured Data Stores Solution Access Groups Business Unit Solution Access Group Co-Located Solutions Co-Located Solution Data Stores Co-Location Identity, Access and Authentication Hosted Shared Solutions Hosted Shared Solution Data Stores Hosted Dedicated Solutions Hosted Dedicated Solution Data Stores Internally Accessible Solutions Externally Accessible Platform Deployed Solutions Internally Accessible Platform Deployed Solutions Publicly Accessible Platform Deployed Solutions Externally Accessible Service Deployed Solutions Internally Accessible Service Deployed Solutions Publicly Accessible Service Deployed Solutions Co-Location Provider Connectivity and Access Outsourced Service Provider Connectivity and Access Outsourced Service Provider Access and Authentication Platform Deployed Solutions Data Stores Service Deployed Solutions Data Stores Data sources outside the organisation boundary providing data to the organisation Public solution consumers outside the organisation and outside the control of the organisation Component providing common facilities for identity and access management and consumer authorisation and authentication Component within cloud service provider for secure connectivity and access to cloud-located solutions and data Component within cloud service providing facilities for identity and access management and consumer authorisation and authentication Solutions deployed in an IaaS pattern designed for use within the organisation Devices owned by the organisation in public locations and from which solutions receive data Devices owned by the organisation in public locations and to which solutions send commands Solution consumers external to the organisation and with whom the organisation has a relationship and who may have authenticated access Employees accessing organisation solutions from outside the organisation’s security boundary Employees accessing organisation solutions outside the organisation but within the organisation’s extended security boundary Interaction areas for secure collaboration with third-parties with authenticated access Solutions hosted on organisation on- premises infrastructure that are publicly accessible without authentication Solutions hosted on organisation on- premises infrastructure that are publicly accessible with authentication Facility to allow the access to organisation data and services and to enable the exchange and transfer of data Component that provides common secure communications facilities to solutions Component that provides facilities to log resource accesses, activities and events Provides protection against viruses and other malware Provides facilities to monitor network access, usage and performance Provides protection against vulnerabilities contained in solutions and any components they use or incorporate Organisation email facility Component that provides common secure identity, authentication and access control facilities to solutions Organisation data backup and recovery facility Set of solution consumers located within a separately located business unit Solutions deployed on on-premises infrastructure designed to be used by internal solution consumers Database-oriented data stores for solutions deployed on on-premises infrastructure Document-oriented data stores for solutions deployed on on-premises infrastructure Set of solution consumers located within the central organisation Component that provides common secure business continuity and disaster recovery facilities to solutions Solutions deployed in an IaaS pattern designed for use outside the organisation Data stores for solutions deployed in an IaaS pattern designed for use within the organisation Solutions deployed in a PaaS pattern designed for use within the organisation Data stores for solutions deployed in an IaaS pattern designed for use outside the organisation by designated external consumers Solutions deployed in a PaaS pattern designed for use outside the organisation by designated external consumers Solutions deployed in a PaaS pattern designed for use outside the organisation by public consumers Solutions deployed in an IaaS pattern designed for use outside the organisation by public consumers Data stores for solutions deployed in an IaaS pattern designed for use outside the organisation by public consumers Data stores for solutions deployed in a PaaS pattern Solutions deployed in a SaaS pattern designed for use outside the organisation by designated external consumers Solutions deployed in a SaaS pattern designed for use outside the organisation by public consumers Solutions deployed in a SaaS pattern designed for use within the organisation Data stores for solutions deployed in a SaaS pattern Component within outsourced service provider for secure connectivity and access to outsourced solutions and data Facility within outsourced service provider for identity and access management and consumer authorisation and authentication Solutions on a shared platform hosted by within outsourced service provider Data stores for solutions on a shared platform deployed within outsourced service provider Solutions on a dedicated platform hosted by within outsourced service provider Data stores for solutions on a dedicated platform deployed within outsourced service provider Component within a co-location service provider for secure connectivity and access to co-located solutions and data Facility within a co-location service provider for identity and access management and consumer authorisation and authentication Solutions hosted by within a co- location service provider Facility within a co-location service provider for identity and access management and consumer authorisation and authentication Access Control Management Inventory and Control of Assets Data Protection Penetration Testing Continuous Vulnerability Management External Data Telemetry Devices External Public Interacting Parties External Data Sources External Telecommand Devices Account Management Access Control Management Data Protection Malware Defense Penetration Testing Continuous Vulnerability Management Account Management Access Control Management Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Account Management Access Control Management Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Private Access Groups External Private Interacting Parties Externally Located Employees Mobile Employees Access Control Management Data Protection Audit Log Management Browser Protection Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Asset Security Access Control Management Inventory and Control of Assets Data Protection Audit Log Management Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Asset Security Inventory and Control of Assets Data Protection Audit Log Management Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Access Control Management Data Protection Audit Log Management Penetration Testing Continuous Vulnerability Management Data Access, Exchange and Service Gateway Secure Communications Access Externally Accessible Solutions Publicly Accessible Solutions Business Continuity and Disaster Recovery Data Management and Backup and Recovery Network Monitoring Access and Activity Logging Identity, Access and Authentication Mail Solution Unstructured Data Stores Solution Structured Data Stores Solution Access Groups Business Unit Solution Access Group Externally Accessible Infrastructure Deployed Solutions Co-Located Solutions Co-Located Solution Data Stores Co-Location Identity, Access and Authentication Hosted Shared Solutions Hosted Shared Solution Data Stores Identity, Access and Authentication Internally Accessible Infrastructure Deployed Solutions Internally Accessible Infrastructure Deployed Solutions Data Stores Hosted Dedicated Solutions Hosted Dedicated Solution Data Stores Publicly Accessible Infrastructure Deployed Solutions Anti-Virus, Malware Defense Threat Protection and Vulnerability Checking Internally Accessible Solutions Externally Accessible Platform Deployed Solutions Internally Accessible Platform Deployed Solutions Publicly Accessible Platform Deployed Solutions Externally Accessible Service Deployed Solutions Internally Accessible Service Deployed Solutions Publicly Accessible Service Deployed Solutions Cloud Service Provider Connectivity and Access Co-Location Provider Connectivity and Access Outsourced Service Provider Connectivity and Access Account Management Access Control Management Audit Log Management Inventory and Control of Assets Audit Log Management Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Access Control Management Data Protection Audit Log Management Penetration Testing Continuous Vulnerability Management Network Management Asset Security Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Asset Security Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Asset Security Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Asset Security Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Solution Monitoring Audit Log Management Solution Monitoring Audit Log Management Browser Protection Email Protection Malware Defense Inventory and Control of Assets Continuous Vulnerability Management Network Management Inventory and Control of Assets Continuous Vulnerability Management Solution Availability, Resilience, Fault Tolerance and Recovery Data Management and Backup and Recovery Outsourced Service Provider Access and Authentication Inventory and Control of Assets Audit Log Management Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Account Management Access Control Management Audit Log Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Platform Deployed Solutions Data Stores Service Deployed Solutions Data Stores Cloud Service Provider Access and Authentication Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Solution Zone Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Data Zone Asset Security Access Control Management Solution Monitoring Inventory and Control of Assets Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Workstation Zone Central Solutions and Access Organisation Asset Security Access Control Management Solution Monitoring Inventory and Control of Assets Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Remote Business Unit Solutions and Access Co-Located Solutions and Access Outsourced Service Provider Solutions and Access Externally Accessible Infrastructure Deployed Solutions Data Stores Publicly Accessible Infrastructure Deployed Solutions Data Stores Inventory and Control of Assets Audit Log Management Malware Defense Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Access Control Management Audit Log Management Email Protection Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Asset Security Account Management Access Control Management Solution Availability, Resilience, Fault Tolerance and Recovery Solution Monitoring Inventory and Control of Assets Data Protection Audit Log Management Application Solution Security Browser Protection Email Protection Malware Defense Data Management and Backup and Recovery Network Monitoring Penetration Testing Continuous Vulnerability Management Network Management Supplier and Service Provider Management Cloud Service Provider Solutions and Access Secure External Organisation Access Secure External Organisation Participation and Collaboration Insecure External Organisation Presentation And Access Audit Log Management Audit Log Management Access Control Management Network Management Account Management Account Management The functional and operational design of any solution and therefore its security will include many of these components, including those inherited by the solution or common components used by the solution. The complete solution security view should refer explicitly to the components and their controls. While each individual solution should be able to inherit the security controls provided by these components, the solution design should include explicit reference to them for completeness and to avoid unvalidated assumptions. There is a common and generalised set of components, many of which are shared, within the wider solution topology that should be considered when assessing overall solution security. Solution Components Solution Landscape Solution Component Zones The sets of components that comprise the extended solution landscape, including those components that provide common or shared functionality, are located in different zones, each with different security characteristics.
