LiPari_MedicalDevices
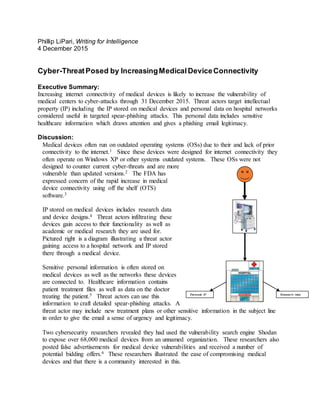
- 1. Phillip LiPari, Writing for Intelligence 4 December 2015 Cyber-ThreatPosed by IncreasingMedicalDeviceConnectivity Executive Summary: Increasing internet connectivity of medical devices is likely to increase the vulnerability of medical centers to cyber-attacks through 31 December 2015. Threat actors target intellectual property (IP) including the IP stored on medical devices and personal data on hospital networks considered useful in targeted spear-phishing attacks. This personal data includes sensitive healthcare information which draws attention and gives a phishing email legitimacy. Discussion: Medical devices often run on outdated operating systems (OSs) due to their and lack of prior connectivity to the internet.1 Since these devices were designed for internet connectivity they often operate on Windows XP or other systems outdated systems. These OSs were not designed to counter current cyber-threats and are more vulnerable than updated versions.2 The FDA has expressed concern of the rapid increase in medical device connectivity using off the shelf (OTS) software.3 IP stored on medical devices includes research data and device designs.4 Threat actors infiltrating these devices gain access to their functionality as well as academic or medical research they are used for. Pictured right is a diagram illustrating a threat actor gaining access to a hospital network and IP stored there through a medical device. Sensitive personal information is often stored on medical devices as well as the networks these devices are connected to. Healthcare information contains patient treatment files as well as data on the doctor treating the patient.5 Threat actors can use this information to craft detailed spear-phishing attacks. A threat actor may include new treatment plans or other sensitive information in the subject line in order to give the email a sense of urgency and legitimacy. Two cybersecurity researchers revealed they had used the vulnerability search engine Shodan to expose over 68,000 medical devices from an unnamed organization. These researchers also posted false advertisements for medical device vulnerabilities and received a number of potential bidding offers.6 These researchers illustrated the ease of compromising medical devices and that there is a community interested in this. Personal IP Research data
- 2. Source Reliability: High Analytic Confidence: Medium Analytic Confidence: The analyst worked with a small group to compile this information. The deadline was reasonable and the information was simple to find. The analyst did not use structured analytic methods. With questions and comments, please contact the author: Phillip LiPari 1 http://gizmodo.com/thousands-of-medical-devices-are-open-to-hacking-over-t-1733961503 (M) 2 https://blogs.microsoft.com/cybertrust/2013/08/15/the-risk-of-running-windows-xp-after-support-ends-april- 2014/ (L) 3 http://www.fda.gov/RegulatoryInformation/Guidances/ucm077812.htm (H) 4 http://www.pabstpatent.com/medical-devices (H) 5 http://www.forbes.com/sites/bernardmarr/2015/04/21/how-big-data-is-changing-healthcare/ (M) 6 http://www.bbc.com/news/technology-34390165 (M)